MSSQL - Microsoft SQL
This section will cover ways to enumerate Microsoft SQL (MSSQL).
Table of Contents
- Overview
- Default Configuration
- Dangerous Settings
- Enumerating MSSQL
- Nmap
- Metasploit
- Impacket-mssqlclient
Overview
Microsoft SQL (MSSQL) is Microsoft's SQL-based relational database management system. MSSQL is closed-source and initially written to run on Windows operating systems. The default port for MSSQL is TCP port 1433 and UDP 1434. However, when MSSQL operates in "hidden" mode, it will use TCP port 2433.
SQL Server Management Studio (SSMS) comes as a feature that can be installed with the MSSQL package or installed separately. SSMS is a client-side application. There are other clients that can be used to access a MSSQL database.
Some such clients are:
- mssql-cli
- SQL Server PowerShell
- HeidiSQL
- SQLPro
- Impacket's mssqlclient.py
Among the listed clients, Impacket-mssqlclient will be the most useful to us.
MSSQL has default systems databases that can help us understand the structure of the database that is being hosted on the target server. The below table will list the default databases and their description.
| Database | Description |
|---|---|
| master | Tracks all system information for an SQL instance. |
| model | Acts as a template for new databases being created. Any changes made in this DB will be reflected in new DBs created. |
| msdb | The SQL Server Agent uses this database to schedule jobs and alerts. |
| tempdb | Stores temporary objects. |
| resource | A Read-only database containing system objects included with SQL server. |
Default Configuration
During initial installation, the SQL service is likely running as NT Service\MSSQLSERVER. Connecting from the client-side is possible through Windows authentication. By default, encryption is also not enforced.
Dangerous Settings
As there are many possible configurations with MSSQL, the following are just some examples of such:
- MSSQL client not using encryption to connect to the MSSQL server.
- Using self-signed certificates.
- Using named-pipes
- Weak and/or default
sacredentials.
Enumerating MSSQL
There are many tools that can be used to enumerate MSSQL.
The following will be covered here:
- Nmap
- Metasploit
- Impacket-mssqlclient
Nmap
The following NSE scripts can be used:
- ms-sql-info
- ms-sql-empty-password
- ms-sql-xp-cmdshell
- ms-sql-config
- ms-sql-ntml-info
- ms-sql-tables
- ms-sql-hasdbaccess
- ms-sql-dac
- ms-sql-dump-hashes
We can use the following Nmap command to enumerate MSSQL.
nmap -sV -sC -p 1433 --script ms-sql* 10.129.70.44
Command breakdown:
-sV- Scan the version.-sC- Use Nmap default scripts.-p 1433- Specify the target port to scan.--script ms-sql*- Specify to use all scripts that starts withms-sql.10.129.70.44- Specify the target IP address to scan.
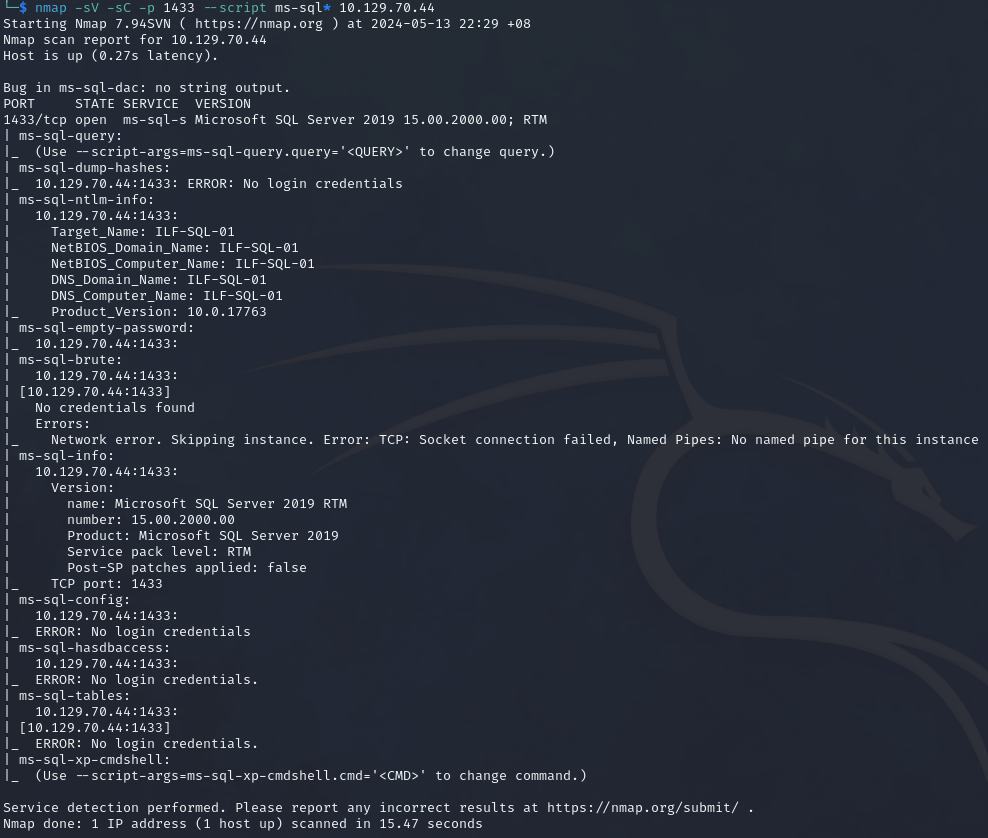
We can provide additional arguments using the --script-args flag as we gather more information.
Metasploit
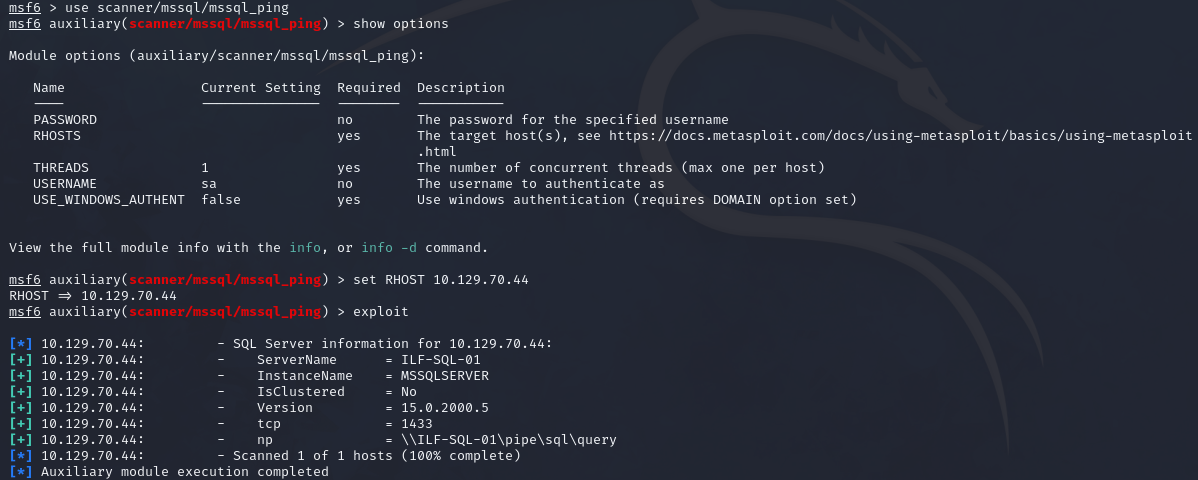
We can use the scanner/mssql/mssql_ping module in Metasploit. To set it up, simply set the RHOSTS to the IP address of the target.
Impacket-mssqlclient
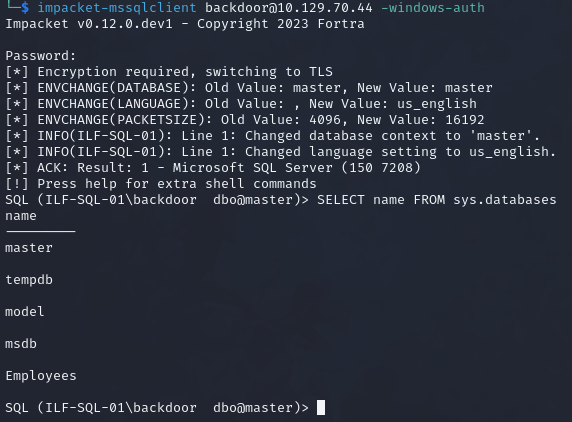
Once we have credentials, we can interact with the server, we can use impacket-mssqlclient.
impacket-mssqlclient backdoor@10.129.70.44 -windows-auth
Command breakdown:
backdoor@10.129.70.44- Specify the username to login as and the target IP address.-windows-auth- Specify to use Windows authentication.